Lost revenue, increased costs, damaged reputation – card testing attacks have the potential to seriously impact an e-commerce merchant’s bottom line.
While credit card fraud has been steadily increasing over the past decade, COVID-19 has fueled an explosive growth in fraudulent activity, with fraud losses expected to reach $38 billion by 2027!
Time to hit the panic button?
Not necessarily.
If detecting and preventing card testing attacks is high on your priority list, there’s nothing to be afraid of!
In this blog, we’ll discuss how card testing fraud impacts your business, how you can spot unauthorized attacks, and what kind of tactics you should use to hackproof your website!
What are card testing attacks?
First things first, what is card testing?
If you’re unfamiliar with the topic, let’s discuss the meaning of card testing attacks first. (If you already know the ins and outs, feel free to jump to the next section!)
Card testing attacks are one of the most common fraudulent activities experienced by websites that accept online payments.
Card testing fraud occurs when cybercriminals get their hands on stolen credit card numbers and try to buy low-priced items online.
Their aim is to test those numbers to see which of the stolen cards are still valid. If a purchase is successful, they’ll know the card is still active and can be used for further fraud.

How do card testing attacks harm your business?
Sadly, the cost of card testing attacks can be substantial for many businesses:
- Disputes – Once card owners notice their cash going missing, they surely won’t be happy. They’ll immediately report the false purchase to their bank. This will lead to disputes that cost you money and time. In many cases, card owners will contact you directly about these charges, and you’ll have to handle the situation personally.
- Transaction fees – When your business is hit by card testing attacks, you’ll have to face substantial revenue losses in many cases. No matter whether the transaction attempts are successful or not, you’ll need to pay transaction fees for each of them. Hundreds or thousands of fraudulent transactions can quickly add up to big losses.
- Chargeback fees – When a fraudulent transaction is initially approved but then disputed by the rightful card owner, you’ll have to pay a chargeback fee. These fees can often exceed the cost of the initial small purchase or donation. The second bad news is that they can also quickly add up when a hacker barrages your site with multiple card testing attempts. The worst-case scenario? These costs can be so high they might even force you to close your business!
- Additional penalties – Card testing attacks can result in additional fees such as authorization fees for custom pricing plans.
- Infrastructure strain – Usually, card testing attacks involve a great number of network requests and operations. This surge in traffic can disrupt legitimate activity.
- Damaged reputation – Card testing attacks might cause your business to be associated with a high decline rate. This might damage your reputation with card issuers and card networks, as your transactions will appear riskier. As a result, you may have to face an increased decline rate for legitimate payments even after the fraud stops, and you might be blacklisted by payment providers as well.
- Increased administrative strain – Finally, card testing attacks might also force your team to spend hours identifying which transactions are actually valid and require shipment, and which are fraudulent and need immediate intervention.
How can you tell if you’ve fallen victim to card testing fraud?
Typically, you’ll see a sharp rise in card authorization volume for low-dollar transactions submitted within a short period of time. These will come from different card numbers. Often, you’ll see multiple transactions from the same card number with different expiration dates each time.
In case of card testing attacks, expect to see an unusually high number of declines as well. Disputes for unauthorized purchases may start rolling in, and within a few days, a large number of chargebacks may show up in your account.
What are the best ways to prevent card testing attacks?
The most important thing to remember is: no single factor can prevent card testing attacks!
Instead, you’ll need to apply a multilayered approach.
The question is: how can you strike a delicate balance between keeping your transaction process simple to maintain high conversions and keeping your customers safe to avoid fraud?
Let’s see the exact steps!
1. Enable Google reCAPTCHA
Your first line of defense to protect against automated transactions on your website should be adding Google reCAPTCHA to your checkout.
Google reCAPTCHA will keep most bots from performing card testing attacks on your website. (Nevertheless, it won’t stop manual testing.)
Legitimate users will be able to create accounts, log in, and make purchases, However, fake users will be blocked.
If you’re using WP Full Pay as your payments plugin for your WordPress site, you can enable reCAPTCHA in 2 simple steps:
Go to “WP Full Pay / Settings” in the WP admin panel and select “Security”:
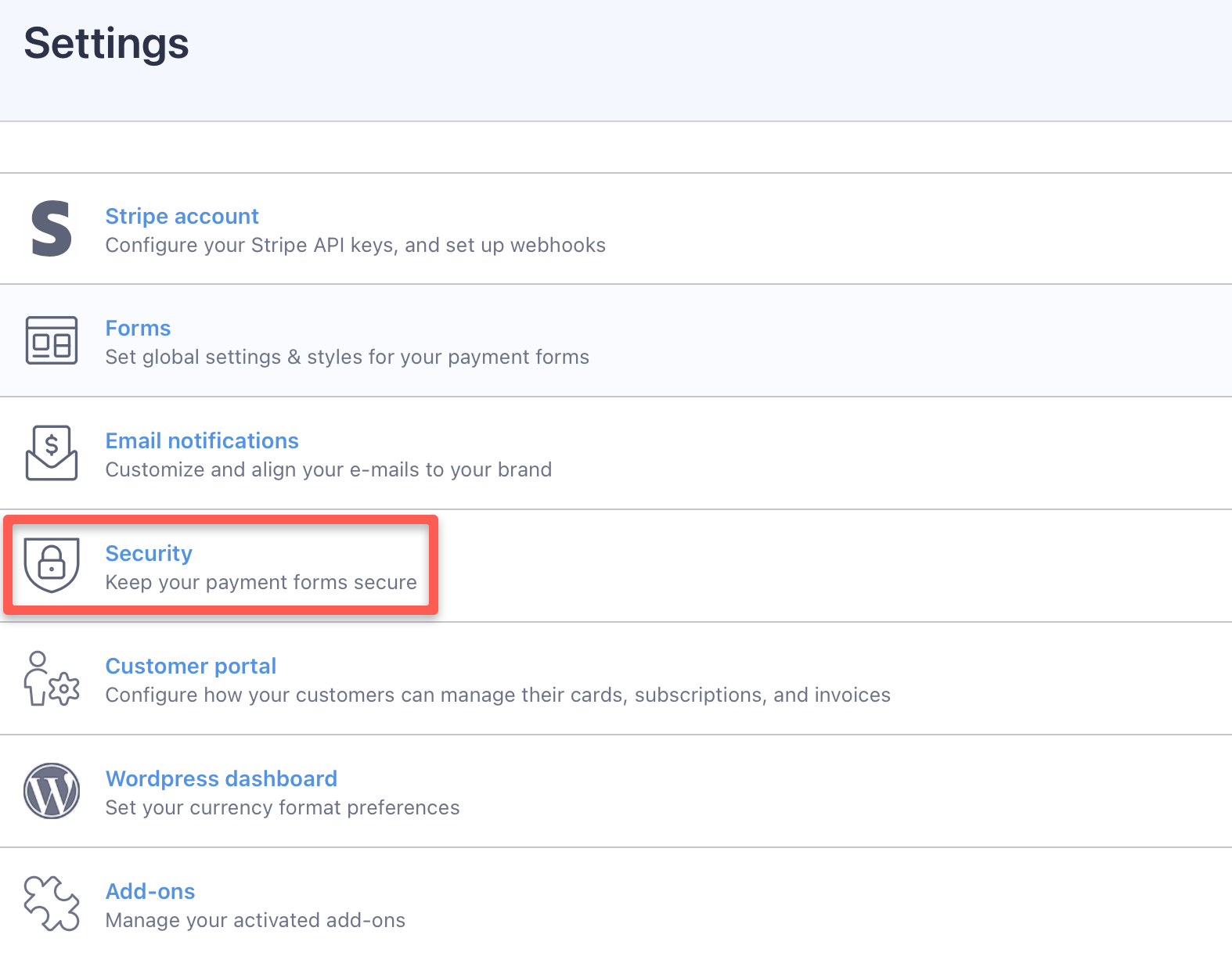
Next, check what you’d like to protect (Stipe checkout forms, or customer portal), and enter the reCAPTCHA API keys:
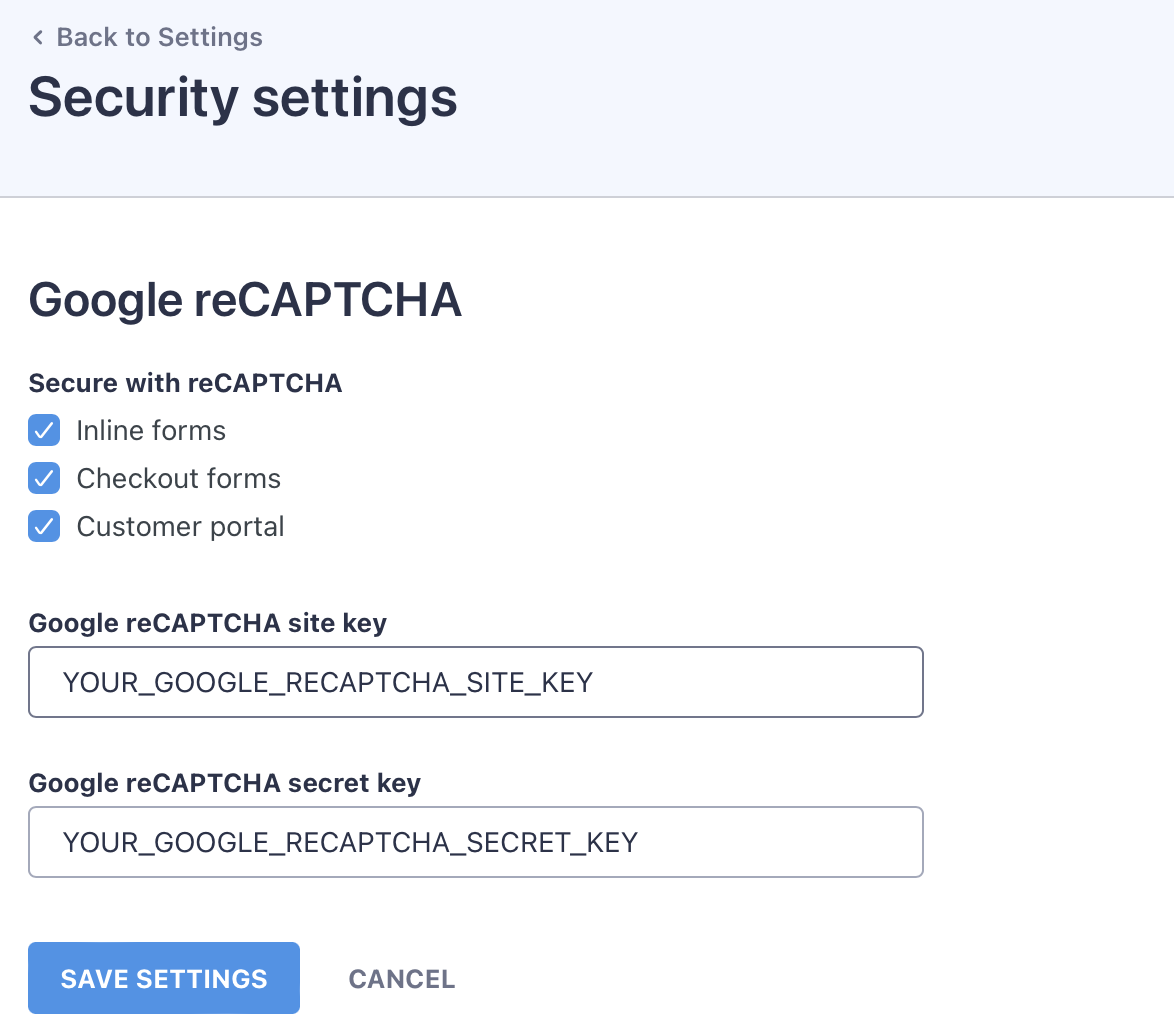
WP Full Pay supports reCAPTCHA v2. You can obtain the API keys here.
2. Set a minimum payment amount
Companies that offer small transaction sizes or microtransactions are an attractive option for hackers, as these kinds of purchases are less likely to be noticed by the seller or the card owner. Also, they’re less likely to be flagged by the bank.
For this reason, forms where the user can set the payment amount are especially exposed to card testing attacks.
Most often, the following types of forms are impacted:
- payment forms to pay invoices where the payment amount can be entered manually;
- donation forms with preset low amounts or custom amounts entered manually.
You might also like to read how to accept donations on WordPress with WP Full Pay.
The solution? Simply set a minimum value in your form. The higher the number the better; however, make sure it doesn’t prevent your honest donors/customers from using your website as designed!
Using WP Full Pay, you can set the minimum payment amount on the “Payment tab” of the form:
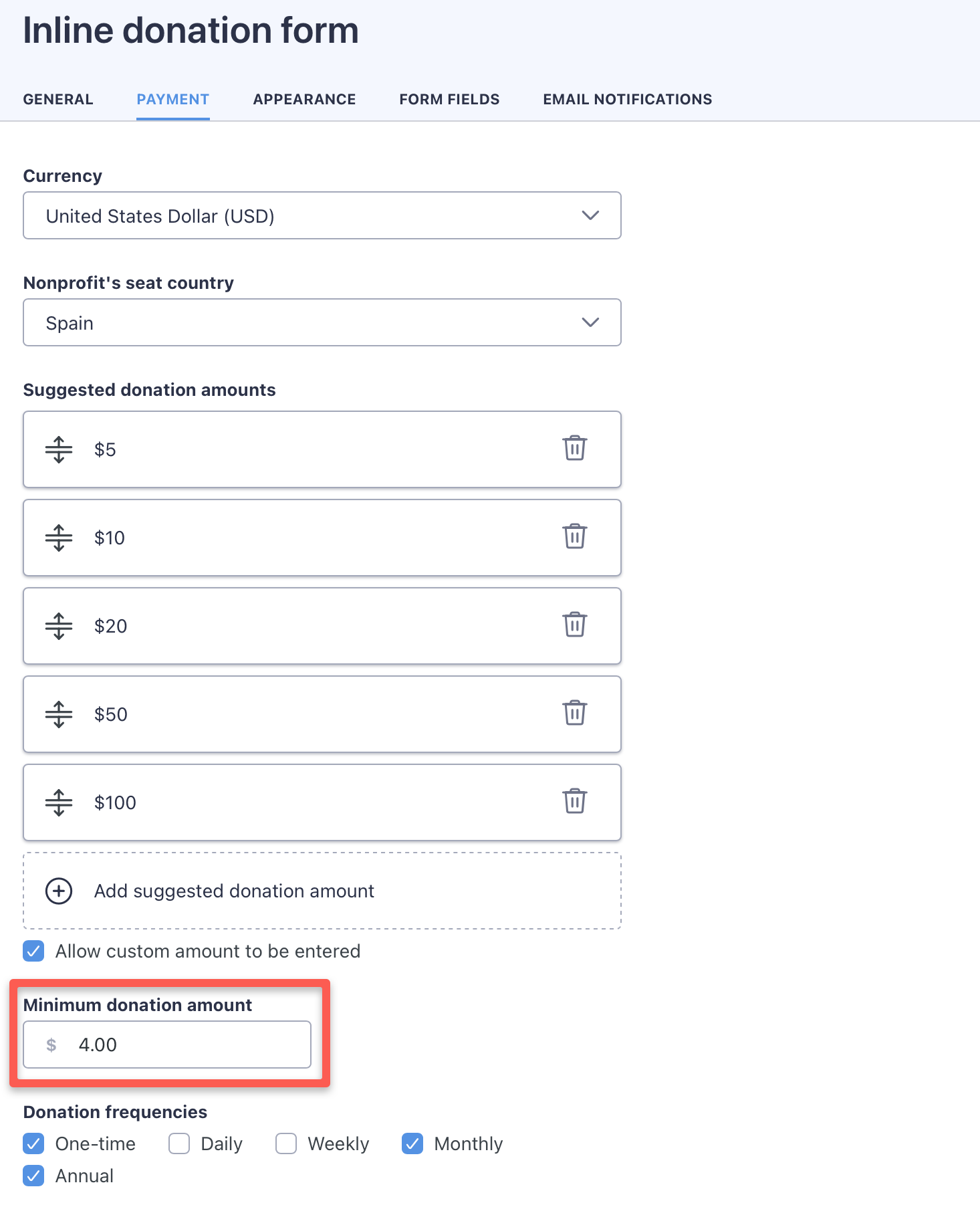
For further tips regarding creating secure forms, make sure to read our secure forms blog post!
3. Require customer registration
As the next step, make sure you discourage card testing attacks by eliminating guest checkout.
The goal is to have all your transactions come from registered customers.
Requiring new users to go through a registration process will discourage card testers from invading your site.
4. Apply velocity checks
Velocity checks are critical to mitigate card testing attacks. They help you monitor specific transaction data elements occurring in specified intervals within a short period of time.
Therefore, you should create a velocity logic ruleset to track specific actions and filter test attempts by IP address, transaction amount, and repetition. These rules help you blacklist any IP addresses that meet your criteria.
For instance, you can create a logic ruleset that sends alerts for small transactions using the same credit card number or IP address multiple times within a short time frame. Or, you can filter an abnormally large number of purchases over a short period of time.
These real-time notifications will allow you to identify anomalies early on and quickly take action.
5. Limit the number of checkout attempts
Another simple technique to prevent card testing fraud is to limit the number of times a user can attempt to complete an order in one shopping cart session.
This way, card testers won’t have the opportunity to test multiple numbers to check data such as addresses, CVV numbers, or ZIP codes.
6. Deploy 3D Secure protocols to authenticate card payments
3D Secure (3DS) offers an additional layer of security used by online business owners to ensure a purchase is from a legitimate cardholder.
The process typically involves an additional 3D Secure step at checkout. The buyer is redirected to the authentication page on their bank’s website. Here, they have to enter a verification code sent to their phone or email.
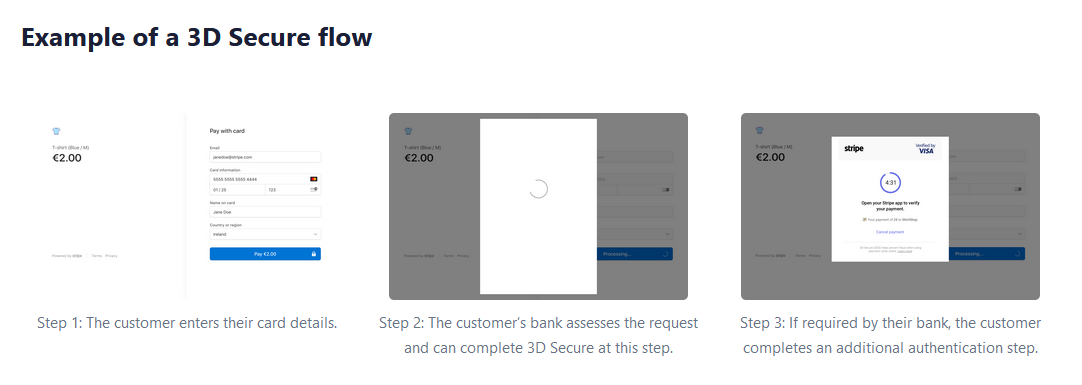
You can decide which transactions require 3D Secure authentication. For instance, you might first filter high-risk transactions and then decide to further secure these with 3D Secure.
7. Partner with the right payment service provider
While the above best practices all play a critical role in fighting card testing attacks, partnering with a secure payment service provider offers a layer of protection you can’t afford to ignore.
Selecting a payment solution with a strong risk management engine and smart fraud prevention tools will give you peace of mind, allowing you to focus on growing your business.
Stripe is definitely one of the most well-known online payment service porviders you can trust. Used by millions of companies of all sizes around the globe, it provides fraud prevention solutions that guarantee an exceptional level of security.
Its smart fraud prevention tool Stripe Radar uses machine learning that trains on data across millions of companies worldwide to detect and block card testing attacks in real time. It also helps you distinguish fraudsters from customers and applies Dynamic 3D Secure to high-risk payments.

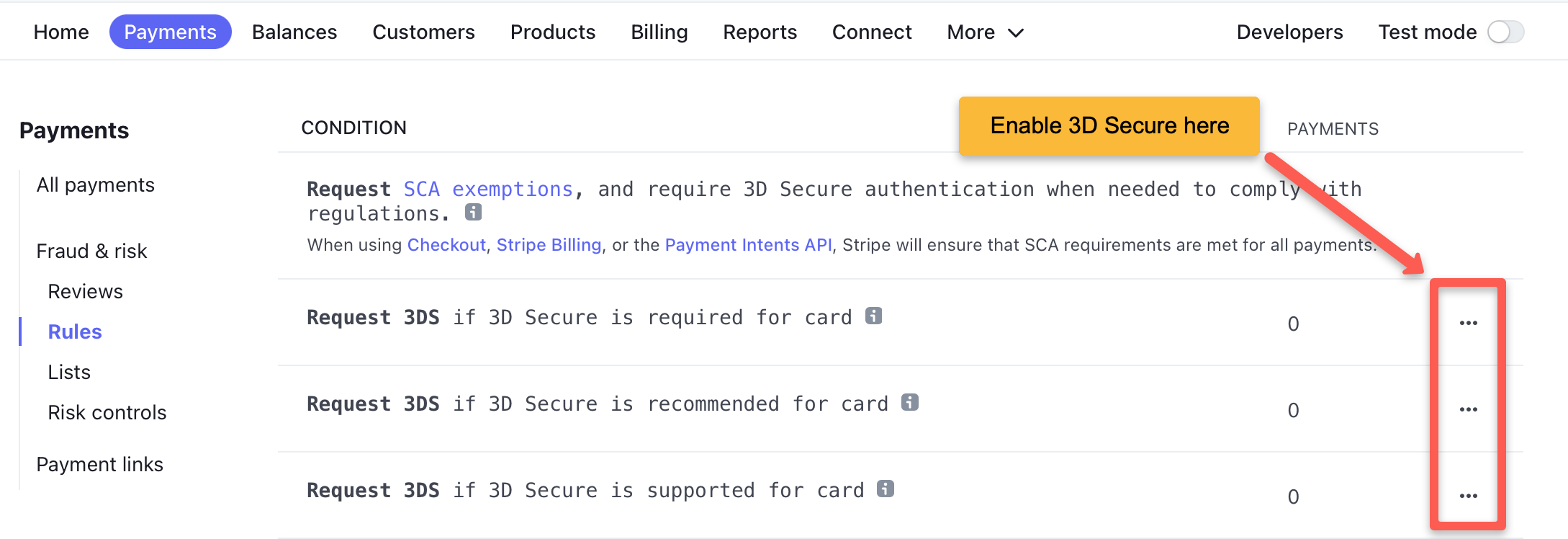
You can enable requesting 3DS on the “Payments / Rules” page of the Stripe dashboard:
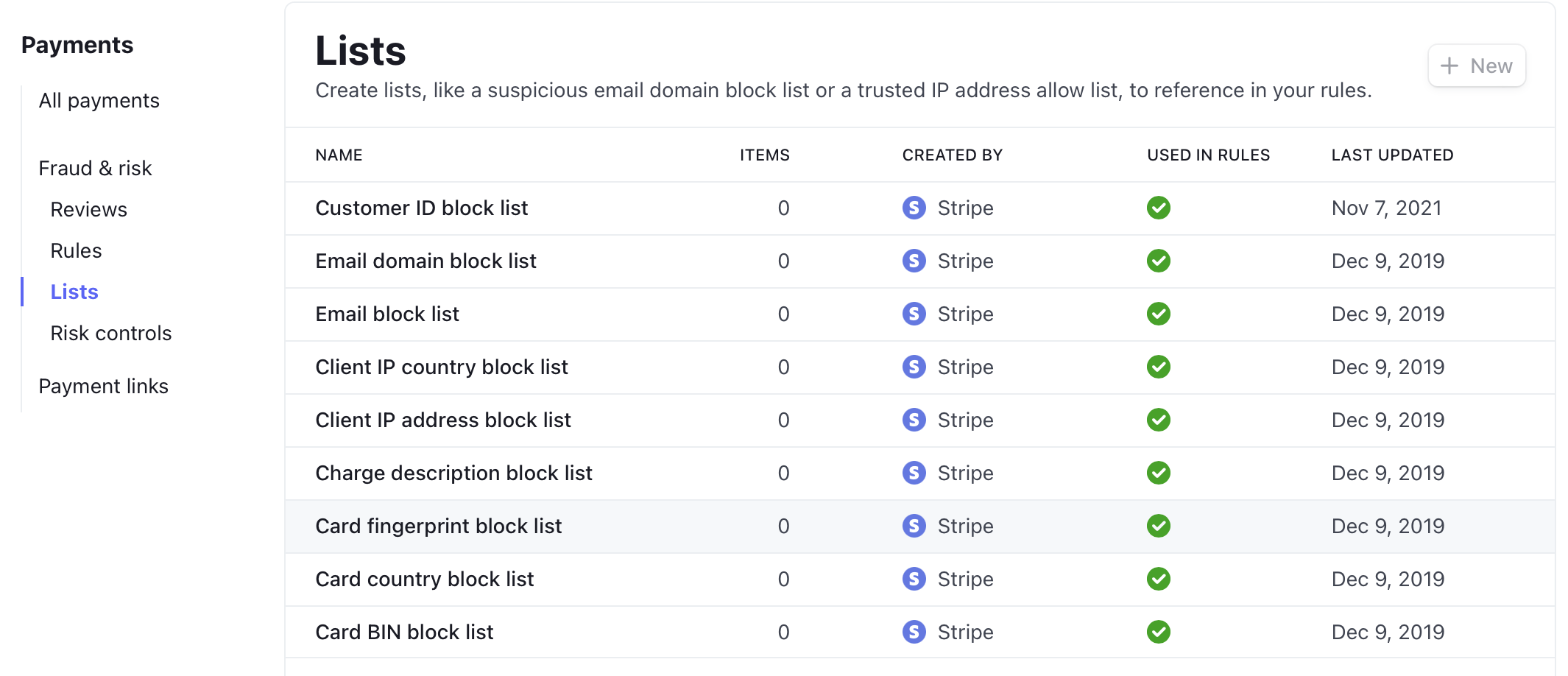
You can set up lists, such as a suspicious IP address block list or card country block list, on the “Payments / Lists” page to reference in your Radar rules:
The bottom line
Failing to detect and block card testing attacks can inflict massive damage on e-commerce merchants. A successful strategy involves applying a multilayered approach to defend your business. The above best practices help you mitigate fraud without compromising conversions.